Nintendo switch tv. Charger for Nintendo Switch, AC Adapter for Nintendo Switch - Fast Travel Wall Charger with 5FT USB Type C Cable 15V/2.6A Power Supply for Nintendo Switch Supports TV Mode and Dock Station 4.7 out of 5 stars 3,566. Connect the USB plug from the Nintendo Switch AC adapter (model No. HAC-002) into the top terminal of the dock labeled 'AC ADAPTER,' then connect the other end of the AC adapter to a wall outlet. Connect one end of the HDMI cable into the bottom terminal of the dock labeled 'HDMI OUT,' then connect the other end into an HDMI port on your. The whole appeal of the Switch, as suggested by the name, is that it can transform from handheld to TV console in seconds. Capable of 720p gaming on the built-in 6.2-inch screen and 1080p when.
- Sophos Xg 18 Mr3 Release Notes
- Sophos Xg 18 Mr3 Pro
- Sophos Xg 18 Mr3 Free
- Sophos Xg 18 Mr3 Review
- Sophos Xg 18 Mr3 Price
- Sophos Xg 18 Mr1
Admins who have already updated their XG firewall to 17.5 MR13 and MR14 have been waiting for this update for quite some time. But also for all others v18 MR3 comes with 34 bug fixes and some new features.
18.0 MRs: New features and enhancements. The new features and enhancements are on this page. The new features and enhancements are on this page. The release notes site describes the new features introduced in XG Firewall 18.0. This section describes the enhancements introduced in Sophos XG. Sophos XG Firewall version 18 MR3 How to export users from the Sophos XG Firewall There is a way to Export Users from the Sophos XG Firewall Export locally created users via Sophos XG Firewall UI.
Upgrade to v18
Currently, there are still two different versions of SFOS being updated by Sophos. There is v17.5 (MR6 — MR14.1) and version 18 (MR1 and MR2).
Users of an XG 85 or XG 105 cannot upgrade to v18 because of insufficient RAM. Therefore, these firewall appliances are also End of Sale and there are corresponding follow-up models. For customers with these older appliances, Sophos continues to keep v17.5 current, at least as far as bug fixes and security updates are concerned.
- Thank you for reaching out to the Community! The firmware version SFOS v18 MR3 is tentatively planned to be released in the second week of September, more info to come.
- Sophos XG Firewall 4 Synchronized Security Security Heartbeat™ - Your firewall and your endpoints are finally talking Sophos XG Firewall is the only network security solution that is able to fully identify the user and source of an infection on your network and automatically limit access to other network resources in response.
To benefit from the latest features, it would be recommended to switch to the new models that support v18. To make it easier for customers with older devices, Sophos is offering a Renewal Promo until the end of the year, giving 50% of the new firewall hardware for free. The other option would be to simply wait until 2021 Q2… (SPOILER: New hardware series will be released. 🤫)
But for firewalls that support v18, an update has not been that easy so far. Until now, there was a working migration path to version 18 only for versions 17.5 MR6 to MR12. Those who had already installed MR13 or MR14 meanwhile were confronted with a factory reset when manually updating to v18 and lost their complete configuration.
With v18 MR3 there is an update path again. We also see with our v17.5 customers that the v18 update on the firewall is suggested automatically for the first time. So, Sophos is confident and has gained enough experience with v18 to make the upgrade available to all customers.
Our experience with v18 and v18 MR3 is also very positive. We recommend an upgrade to v18. 🙌
Why v18 is a fantastic release
The same firewall appliance has also become much faster with the software upgrade to v18! 🚀
On the 100 series (XG 86 - XG 135) the web interface has become quite a bit faster, but on the bottom line it is still **damn slow! 🐌
VPN performance improvements
SSL VPN performance has been improved with v18 MR3. Now, much more parallel connections are supported on the larger hardware models than on the older SFOS version.
Secure Storage Master Key (SSMK)
If you have completed the update and then log in as admin, the following display appears:
Background to this changes
Sophos found a vulnerability in SFOS several months ago. Even further back there was the problem that with some effort the administrator password could be read from the backup files. As a result, backup encryption was also implemented. Sophos takes this issue very seriously and has put a lot of effort into preventing this from happening again. The planned roadmap was shifted by half a year and the first thing they took care of was the security of their system. The incidents have shown that even a firewall, which is supposed to protect against threats, is vulnerable.
The saying “100% security does not exist” does not exist without reason. Many movies or series would be very boring if such a 100 percent security would exist. 😋
Now with v18 MR3 there is the Secure Storage Master Key. This key can only be created with the admin user. This does not work with another user who has administrator rights. With the definition of this new key, important information is encrypted again. If you want to know exactly what happens here, you can read the Secure Storage Dokument.
So create a secure password and store it securely as well.
Disable captcha
The login window of the firewall has been protected with a captcha since the above mentioned vulnerability for the UserPortal and Admin login.
With MR3 this bot protection can be disabled. To do this, you have to log on to the firewall over SSH and switch to the console with keyboard input ‘4’.

Here you can activate, deactivate or display the captcha setting for the login windows with the following command.
Sophos Xg 18 Mr3 Release Notes
Device Access warnings
Like the two functions above, the Device Access warnings are also intended to provide more security.
In the menu: ‘Administration > Device Access’ you can define the access to the firewall services.
Here you should proceed according to the following principle: Close everything and open consciously. For example, by activating the checkbox at ‘Ping’ or ‘User Portal’, you allow every computer worldwide to access your firewall via ICMP or User Portal.
Of course you can change the settings as before. Now the system shows a warning message. This should make you aware of what you can open to the outside world by activating a checkbox in the WAN zone.
It is better to define more precisely where the traffic is allowed from with the ‘Local service ACL exeption rule’. For example, select only your country for accessing the user portal or, when pinging, only those IPs that are actually allowed to reach the firewall via ICMP.
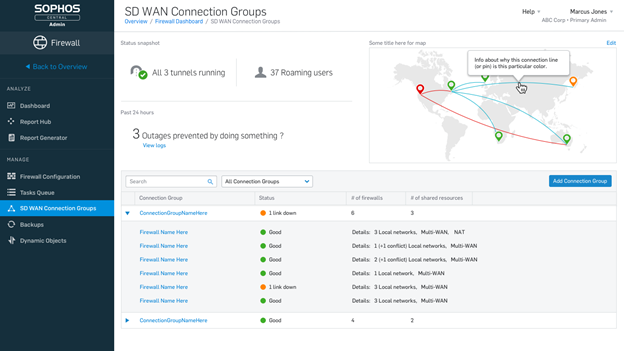
Sophos Central Firewall Management
High Availability Cluster view
All listeners to our podcast know that the Central Firewall Manager is a product in which I see a lot of potential. You can still see that it’s under development, but with v18 MR3 a really nasty thing is fixed.
HA clusters are now no longer displayed as online and offline devices, but you can now easily see which firewalls have been configured to a cluster.
If you click with the mouse on the status display, you will be shown even more information. This shows that this device is in an active-passive cluster and that it is the Auxiliary Device.
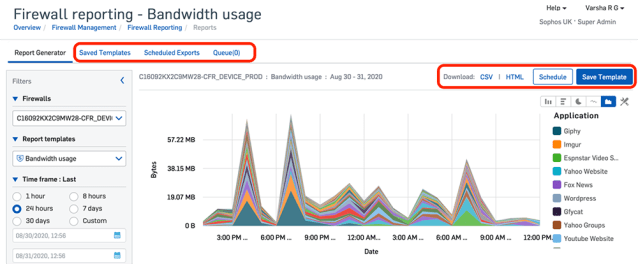
Scheduled Updates
Sophos Xg 18 Mr3 Pro
It is now possible to schedule firmware updates via the Central Firewall Manager. UTM Admins know this from the past.
For a planned update, you can also select multiple firewalls simultaneously, which is a huge benefit in larger environments.
Nevertheless, this feature should be used with caution. An update can also cause problems.
In the screenshot above you can see that there are still some updates to be installed in this environment. 😅
If a firewall is in an update process, this is signaled by an animated icon in the overview. With a click on it you get even more information.
Other enhancements
There are more functions in this release, but I won’t go into detail about them. But for completeness, I will list them:
- Sophos Connect Client: You can now add groups instead of just individual users.
- SFOS now also supports the infrastructure of Nutanix AHV and Nutanix Flow
- AWS: Support for new instances in the AWS Cloud (C5, M5 and T3)
- AWS: Support of CloudFormation Templates
- AWS: Support for Virtual WAN Zones on custom gateways
Sophos XG is a powerful firewall platform that’s designed for business/enterprise use but also offers a Home version that has most of the same features with a few exceptions (i.e. sandstorm). While most of the default settings should suffice, here are some settings I change with a new install of Sophos XG for a fairly basic home network (no servers). This is based on Sophos XG V17-MR3.
Sophos Xg 18 Mr3 Free
Note: Anytime you change a setting, be sure to click ‘Apply’ on the very bottom of the web browser.
1. Browse to the ‘Administration’ page under ‘System’ and select the ‘Device Access’ tab. Uncheck ‘User Portal’ on the ‘WAN’ line in the ‘Local Services ACL’ section. This is enabled by default and allows users to access the User Portal page from outside your network by opening port 443.
2. Browse to the ‘Administration page under ‘System’ and select the ‘Time’ tab. Select ‘Use pre-defined NTP server’. This will keep the Sophos XG time up-to-date with a Network Time Protocol (NTP) server.
3. Browse to the ‘System Services’ page under ‘Configure’ and select the ‘Log Settings’ tab. Uncheck ‘Invalid Traffic’ in the ‘Firewall’ section under ‘Log Settings’. If you keep this enabled, you will see a significant amount of entires in your Log Viewer with the message, “Could not associate packet to any connection”. More information is provided in this Sophos Knowledge Base Article.
4. Browse to the ‘System Services’ page under ‘Configure’ and select the ‘Traffic Shaping Settings’ tab. Set your ‘Total Available WAN Bandwidth’ to match your internet connection speeds. Note that these values are in KBps (KiloBytes per second) and not Kbps (Kilobits per second). Most internet speed tests show you results in Mbps (Megabits per second) but you can easily convert this to KBps using an online convertor such as on Google (search for ‘Mbps to KBps’ on Google).

5. Browse to the ‘Advanced Threat’ page under ‘Protect’ and the first tab you’ll be on is the ‘Advanced Threat Protection’. Set the ‘Enable Advanced Threat Protection’ to ‘ON’. Set the ‘Policy’ to ‘Log and Drop’. According to the Sophos XG Knowledge Base, Advanced Threat Protection (ATP) “can help rapidly detect infected or compromised clients inside the network and raise an alert or drop the traffic from those clients.”
6. Browse to the ‘Intrusion Prevention’ page under ‘Protect’ and select the ‘DoS & Spoof Protection’ tab. Scroll down to the ‘DoS Settings’ and enable ‘ARP Hardening’. This will restrict your devices from sending an Address Resolution Protocol (ARP) reply only if the destination IP is a local address and both the sender and destination IP address are in the same subnet. Basically, ARP replies will only be allowed within the same subnet.
Sophos Xg 18 Mr3 Review
7. Browse to the ‘Email’ page under ‘Protect’ and select the ‘General Settings’ tab. Click the ‘Switch to Legacy Mode’ button under ‘SMTP Deployment Mode’. I’m still trying to learn the difference between the two modes and the benefit of using one or the other if you’re not running an email server at home. The reason I switched to Legacy Mode is because I was unable to send any email when it was in MTA mode. Additionally, on this same page, scroll down to the ‘SMTP TLS Configuration’ and ‘POP and IMAP TLS Configuration’ sections and enable ‘Disable Legacy TLS protocols’ in both sections. As the description next to the option mentions, this is recommended to overcome TLS vulnerabilities by disabling protocols lower than TLS1.1.
Sophos Xg 18 Mr3 Price
8. While you can use the DNS servers provided by your ISP, I prefer to use different DNS servers for better performance and increased privacy. You can use a tool such as namebench to determine which DNS servers will provide the best performance and some research to decide which DNS servers will suit your needs (Cloudflare, Google, OpenDNS, Quad9, etc.). Browse to the ‘Network’ page and select the ‘DNS’ tab. Under the IPv4 section, select ‘Static DNS’ and enter the DNS servers you prefer. Personally, I use CloudFlare’s DNS servers of ‘1.1.1.1’ (DNS 1) and ‘1.0.0.1’ (DNS 2), and Google’s DNS server of ‘8.8.8.8’ (DNS 3). You can leave the IPv6 fields blank but if you want to add the IPv6 addresses, they are ‘2606:4700:4700::1111’, ‘2606:4700:4700::1001’ and ‘2001:4860:4860::8888’ for Cloudflare (DNS 1 & 2) and Google (DNS 3). Leave the ‘DNS Query Configuration’ set to ‘Choose server based on incoming request type’.
Sophos Xg 18 Mr1
Note: If you decide to use a separate DNS server such as Pi-hole, the Sophos XG DNS server is still being utilized by the pharming protection feature which is enabled by default (‘Web’ -> ‘General Settings’ -> ‘Advanced Settings’). I use Pi-hole as my DNS server but leave pharming protection enabled to help protect against domain name poisoning attacks.
